From F to B
in Mozilla’s Observatory Security Report
The Trinity Technology Services system administrators implement changes to Varnish to dramatically improve our Drupal website’s security.
- Kyle Skrinak
- David Palmer
- Blaine Ott
1 / 12
The Problem
- ITSO sends TTS NetSparker report
- We break out the Drupal Security Kit module
- We create a test configuration and ask for another scan
- NetSparker is now busy, ITSO recommends Observatory
2 / 12
3 / 12
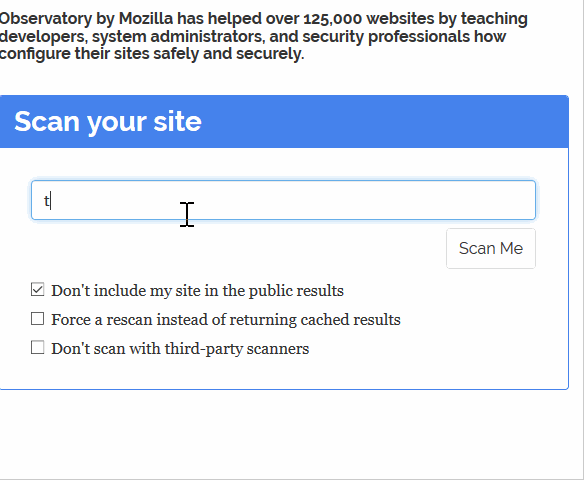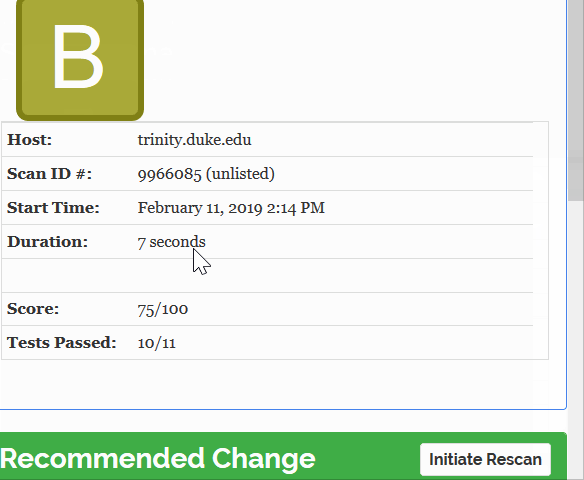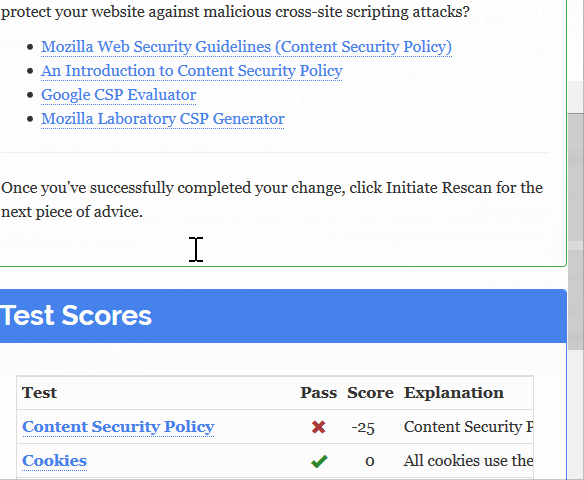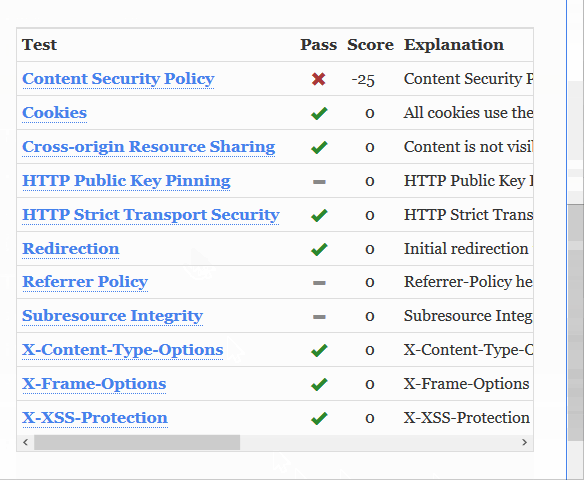
Original website results
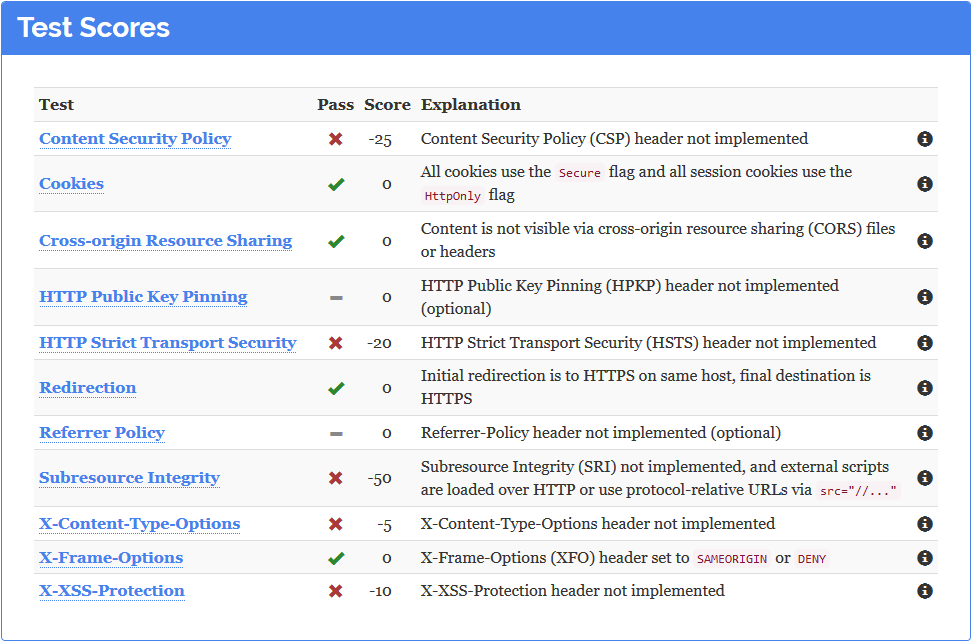
4 / 12
Eureka!
Why have MySQL + PHP do something apache can do?
Why have apache do something that varnish can do?
5 / 12
Our First Attempt
### TTS Apache Hardening
set resp.http.X-XSS-Protection = "1; mode=block";
set resp.http.Strict-Transport-Security= "max-age=31536000; includeSubDomains";
set resp.http.X-Content-Type-Options = "nosniff";
6 / 12
Oops
We inadvertently blocked fourth-level domains
7 / 12
Info pages for HSTS configuration options
- A link to Mozilla’s HTTP Strict Transport Security information page.
8 / 12
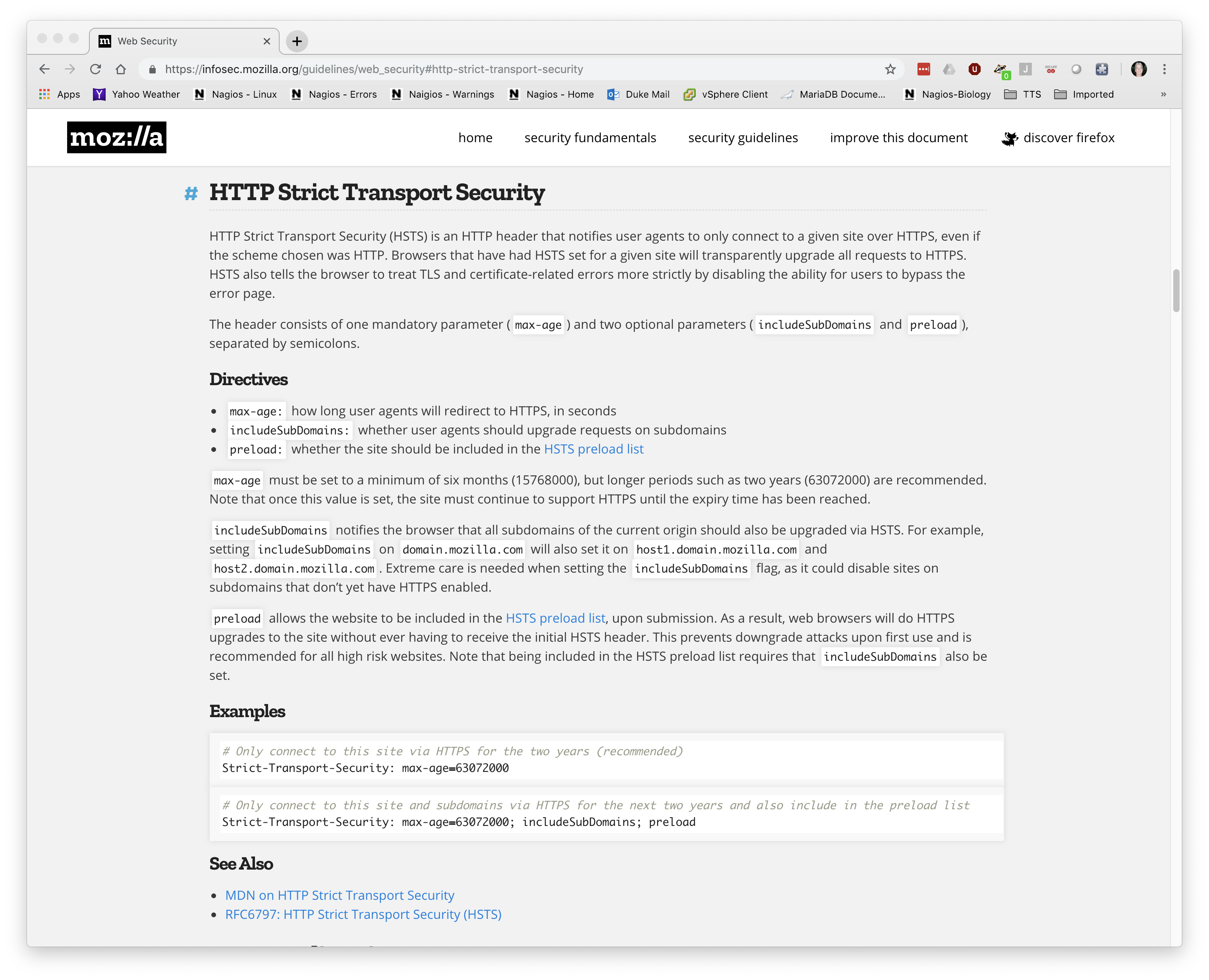
9 / 12
- A link to Redhat’s HSTS configuration page.
10 / 12
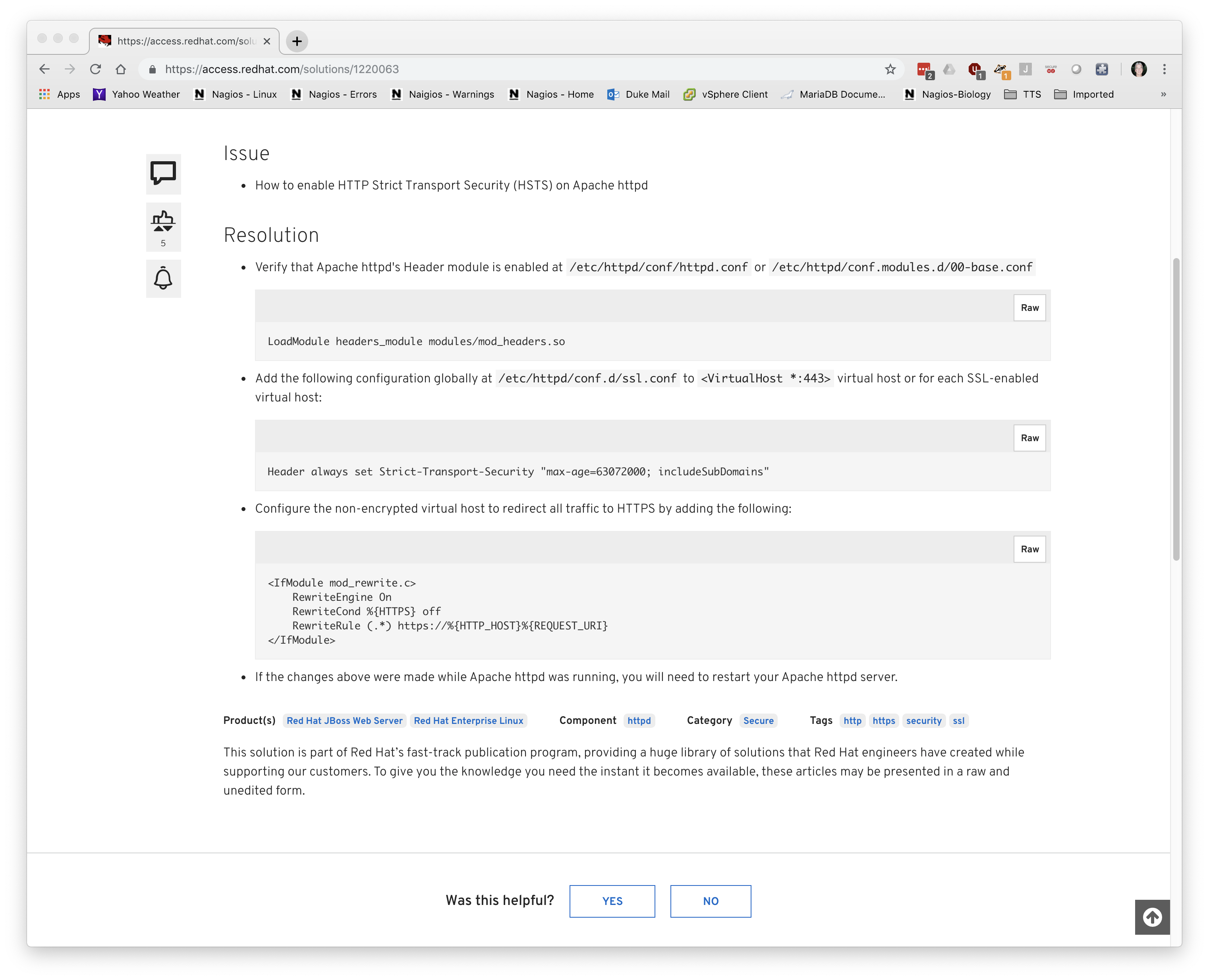
11 / 12
Questions?
12 / 12